In this article, I’ll answer the questions:
- What is email spoofing?
- How do spammers spoof an email address?
- What does a spoofed email look like?
- How can you prevent email spoofing?
According to Proofpoint, 3.1 billion spoofed emails are sent every day, with attacks costing businesses $26 billion (about £18.8 billion) since 2016. The goal of email spoofing is like phishing, as fraudsters attempt to obtain sensitive information from the recipient or get them to download a malicious attachment. However, instead of simply imitating the email address of a trusted source, spoofed emails manipulate the way emails are delivered.
How do spammers spoof my email address?
Email spoofing is possible because of the way email providers send and deliver messages. When someone sends an email, it doesn’t simply go from the person who created the message to the intended recipient. Rather, it goes through an SMTP (Simple Mail Transfer Protocol) server configured in the client software.
You can think of this process like a sorting office for physical post. The SMTP takes an incoming message and routes it to the relevant email server, which then directs it to the relevant user inbox. This gives criminal hackers the opportunity to input a bogus address in the ‘Sent’ field, because the SMTP doesn’t have a process to authenticate this information. As such, attackers can make it look as though the email has been delivered from someone else.
What does a spoofed email look like?
Now we’ve answered the question ‘what is email spoofing?’, let’s examine what a spoofed email looks like. Below is a real-world example of a spoofed email received by multiple members of the ESA Risk team last week, purporting to be from ESA Risk’s Marketing Director. This email was caught by our spam filters, so it didn’t make it into anyone’s inbox, but it did arrive in their spam folder, so required manual intervention to fully eliminate the potential threat.
—–Original Message—–
From: xxxxxxx@staging.esarisk.com <rebeccasmith0900@gmail.com>
Sent: 20 October 2021 08:25
Subject: RAPID INTERVENTION
Good morning,
Hope you don’t have a lot of work to do? Well in case you do, peg it now because i have a task for you to carry out urgently.
Drop your number so i can brief you about it all.
Thanks.
Xxxx xxxxxxxxxxx @staging.esarisk.com
Sent from iphone
Spot the obvious issues with the above.
Here is another example of what someone might see when they receive a spoofed email:
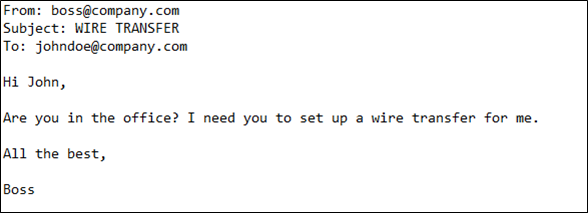
There is nothing here that reveals the true nature of this message. The ‘From’ field displays the address provided by the scammer, but, crucially, this is not necessarily the email address from which the message originated. Only by investigating the email header (sometimes known as the envelope) can you tell if the ‘From’ field has been manipulated. This information isn’t typically displayed on email clients and will require you to look in your settings.
In most versions of Outlook, you can do this by double-clicking the message to get it to open in a separate window, then selecting ‘File’ and ‘Properties’. You’ll be presented with a long string of information, but within that you should see something that looks like this:

You can see here that, although the message says it’s from the employee’s boss, there is a different address in the reply field. When the recipient responds, the message isn’t going to ‘boss@company.com’ but to ‘scammer@scammail.com’. This is a big clue that the original email address has either been forged or compromised. A bogus email address won’t always be as easy to spot, however. You may well encounter the same technique as standard phishing attacks, with the attacker replicating the email address of a genuine organisation.
In this example, the sender might register the email domain ‘conpamy.com’ – transposing the ‘n’ and the ‘m’. This can be tricky to spot, and it’s why organisations should adopt SPF (Sender Policy Framework). SPF is a security protocol that works alongside DMARC (Domain-based Message Authentication, Reporting and Conformance) to detect malware and phishing attacks. It does so by comparing the IP address from which the email was sent to the address in the ‘From’ field.
If you’ve implemented SPF, the email header will contain a string of text that looks like this:
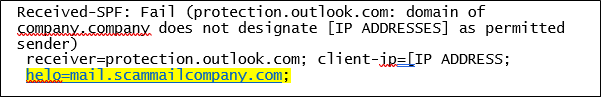
You can see that this message failed the test, because the client’s IP is not permitted to send messages from the company domain. Implementing SPF helps flag suspicious emails and reduces the burden on employees to spot scams. However, for it to work, the domain holder (which in most circumstances will be your organisation) must configure a DNS TXT entry specifying all IP addresses authorised to send email on behalf of the domain.
How to prevent email spoofing and what to do if your email has been spoofed
At this point, I’m sure you’re asking the question: ‘How can I stop spoofing emails coming from my email address?’ Technical solutions such as SPF can help protect organisations from email spoofing. They can be implemented alongside spam filters and anti-malware software to give you the best chance of flagging suspicious messages before they reach employees’ inboxes.
However, these tools are never foolproof, and scammers are always finding clever ways to bypass security mechanisms and they may ask you the recipient to confirm that the email is real and valid, so it’s down to the recipient to decide. As such, you must ensure that employees are trained to detect, and respond appropriately to, suspicious emails.
Phishing emails always contain clues that can help you spot their true nature and ESA Risk provide training for you and your teams on these issues and all things cyber security.
If your email has been spoofed, you want to prevent email spoofing or you have any other cyber security questions or concerns, please contact us at advice@esarisk.com, on +44 (0)343 515 8686 or via our contact form for advice.

Get the advice you need
Our expert consultants are on hand to give you the support you need.